Yes, it’s possible! Tested on Windows Server 2016.
LDAPS Certificates are always be a little mistery for me. When you search on google you always find big guides that spoke about install the CA authority and deploy certificates.
I have finaly understand that this is not necessary, and as I suspected LDAPS works like any other services exposed trought SSL certificates, like https.
The first mistery was where certificate of LDAPS services was stored, there:
mmc.exe -> File add snap-in -> Certificates -> Service account -> Local computer -> Active Directory Domain Services
Active Directory Domain Services also called NTDS
You can now load Certificate on NTDS\Personal\Ceterificates and Active Directory LDAPS use it automatically after reboot or with a special command.
That is, easy, finaly.
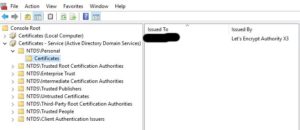
And for Let’s Encrypt? Now…:
As the place where LDAPS cert store it’s not so “easy” to find, also doesn’t exit the powershell command to import certificate to the NTDS/Personal Store, so you need to import to Local Computer and after move it from registry (yes, absurd but working…).
powershell ldaps-cert.ps1 that download Let’s Encrypt exported certificate and call import-ntds.ps1 for load on Local Computer certificate store and after move it to NTDS Store:
Start-Transcript -path log.txt -append Get-Date -Format "dddd MM/dd/yyyy HH:mm K" $cur = Get-Location Write-Host $cur Invoke-WebRequest "[URL_TO_DOWNLOAD_CERTIFICATE_PFX]" -OutFile "donwload.pfx" -PassThru Start-Sleep -Milliseconds 500 $cert = "$cur\download.pfx" Write-Host $cert .\import-ntds2.ps1 $cert [EXPORT PASSWORD] Start-Sleep -Milliseconds 1500 ldifde -i -f ldaps-reload.txt Stop-Transcript
powershell import-ntds2.ps1 called by ldaps-cert.ps1:
using namespace System.Security
[CmdletBinding()]
param (
[parameter(mandatory=$true)] [string] $CertificateFile,
[parameter(mandatory=$true)] [string] $PrivateKeyPassword
)
# Setup certificate
$Flags = [Cryptography.X509Certificates.X509KeyStorageFlags]::MachineKeySet `
-bor [Cryptography.X509Certificates.X509KeyStorageFlags]::PersistKeySet `
-bor [Cryptography.X509Certificates.X509KeyStorageFlags]::Exportable
$Certificate = New-Object Cryptography.X509Certificates.X509Certificate2($CertificateFile, $PrivateKeyPassword, $Flags)
# Install certificate into machine store
$Store = New-Object Cryptography.X509Certificates.X509Store(
[Cryptography.X509Certificates.StoreName]::My,
[Cryptography.X509Certificates.StoreLocation]::LocalMachine)
$Store.Open([Cryptography.X509Certificates.OpenFlags]::ReadWrite)
$Store.Add($Certificate)
$Store.Close()
Write-Host $Certificate.thumbprint
$thumbprint = $Certificate.thumbprint
$copyParameters = @{
'Path' = "HKLM:\Software\Microsoft\SystemCertificates\MY\Certificates\$thumbprint"
'Destination' = "HKLM:\SOFTWARE\Microsoft\Cryptography\Services\NTDS\SystemCertificates\My\Certificates\$thumbprint"
'Recurse' = $true
}
Copy-Item @copyParameters
I have tested that LDAPS Service use always the last added certificate (or the “longer” expire), so it’s not a problem if there are old certificates on the NTDS store.
Add a schedule task that every week launch ldaps-cert.ps1 and the LDAPS cert will be always up to date.
The last part: generating the pfx from a machine with a let’s encrypt working configuration (maybe a linux with apache and https correctly configured), ldaps-cert.ps1 will download from it:
#!/bin/bash /usr/bin/openssl pkcs12 -export -passout pass:[PASSWORD} -out /var/www/html/export/download.pfx -inkey /etc/letsencrypt/live/[DOMAIN]/privkey.pem -in /etc/letsencrypt/live/[DOMAIN]/fullchain.pem chmod 644 /var/www/html/export/*.pfx
Add a cronjob that every week will generate the pfx updated certificate.
Test ssl connection with openssl comands:
openssl s_client -connect [ADLDAPS_PUBLIC_DOMAIN]:636 -showcerts CONNECTED(00000003) depth=2 O = Digital Signature Trust Co., CN = DST Root CA X3 verify return:1 depth=1 C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3 verify return:1 depth=0 CN = [YOUR DOMAIN] verify return:1
Reload LDAPS cert without reboot: ldaps-reload.txt, called from ldaps-cert.ps1 with: “ldifde -i -f ldaps-reload.txt”
dn: changetype: modify add: renewServerCertificate renewServerCertificate: 1 -
Yea!